Updated as of 2:56 PM
As of May 16, 2017, a staggering number of approximately 300,000 enterprises were attacked and is still being attacked by one of the most malicious cybercrime ever committed in the history of the internet: The “Wanna Decryptor” or simply “WannaCry” ransomware. What’s alarming is that, according to Vox, this might just be the start as new variants of the ransomware are on the works.
This ransomware spreads by using a vulnerability in implementations of Server Message Block (SMB) in Windows systems. This exploit is named as ETERNALBLUE. It encrypts the computer’s hard disk drive and then spreads laterally between computers on the same LAN. The ransomware also spreads through malicious attachments to emails.
The following screen will appear after WannaCry infected:
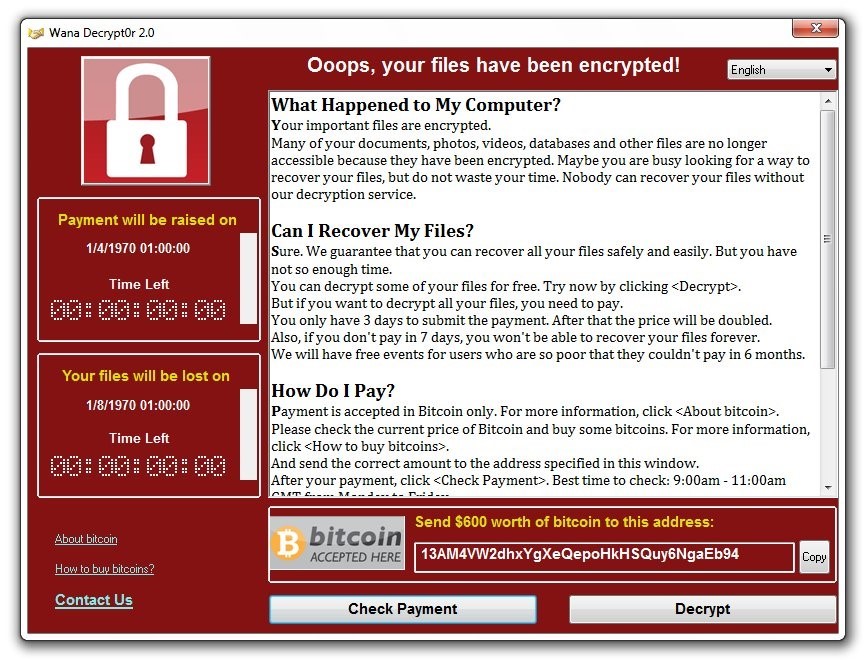
The concept of the attack is simple: WannaCry disguises itself as a harmless application or email attachment waiting for one click to open it. Once it’s activated, it exploits a vulnerability and encrypts all the user’s files. WannaCry then asks the user to pay in $300 in bitcoins within 72 hours or see their files deleted permanently.
There are two attributes that makes WannaCry a devastating malware: it’s both a deadly ransomware and an easy-to-spread worm. All it takes is one infected machine to bring the whole network down. It has affected corporate businesses, public transportation, and even hospitals by totally getting hold of their files and stopping operations. According to BBC News, the most susceptible ones are those operating on outdated systems like Windows XP or even Windows 7 and 10 that refuses to install regular updates.
How to protect yourself from the worst ransomware in history.

Ransomware attacks are common all throughout history, but WannaCry is unique because of the way it targets its attacks: individual machines rather than large scale, multi-million dollar schemes. According to Sumann Subramaniam, Enterprise Security Expert at Tech One Global, the best course of action against the epidemic is prevention. Aside from keeping everything updated, another crucial step is to apply the Microsoft Patch for the MS17-010 SMB vulnerability dated March 14, 2017.
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
The attack starts by encrypting files with the following extensions:
.doc, .docx, .xls, .xlsx, .ppt, .pptx, .pst, .ost, .msg, .eml, .vsd, .vsdx, .txt, .csv, .rtf, .123, .wks, .wk1, .pdf, .dwg, .onetoc2, .snt, .jpeg, .jpg, .docb, .docm, .dot, .dotm, .dotx, .xlsm, .xlsb, .xlw, .xlt, .xlm, .xlc, .xltx, .xltm, .pptm, .pot, .pps, .ppsm, .ppsx, .ppam, .potx, .potm, .edb, .hwp, .602, .sxi, .sti, .sldx, .sldm, .sldm, .vdi, .vmdk, .vmx, .gpg, .aes, .ARC, .PAQ, .bz2, .tbk, .bak, .tar, .tgz, .gz, .7z, .rar, .zip, .backup, .iso, .vcd, .bmp, .png, .gif, .raw, .cgm, .tif, .tiff, .nef, .psd, .ai, .svg, .djvu, .m4u, .m3u, .mid, .wma, .flv, .3g2, .mkv, .3gp, .mp4, .mov, .avi, .asf, .mpeg, .vob, .mpg, .wmv, .fla, .swf, .wav, .mp3, .sh, .class, .jar, .java, .rb, .asp, .php, .jsp, .brd, .sch, .dch, .dip, .pl, .vb, .vbs, .ps1, .bat, .cmd, .js, .asm, .h, .pas, .cpp, .c, .cs, .suo, .sln, .ldf, .mdf, .ibd, .myi, .myd, .frm, .odb, .dbf, .db, .mdb, .accdb, .sql, .sqlitedb, .sqlite3, .asc, .lay6, .lay, .mml, .sxm, .otg, .odg, .uop, .std, .sxd, .otp, .odp, .wb2, .slk, .dif, .stc, .sxc, .ots, .ods, .3dm, .max, .3ds, .uot, .stw, .sxw, .ott, .odt, .pem, .p12, .csr, .crt, .key, .pfx, .der
According to Sumann, WannaCry changes file extensions to “.wcry.” and locks them.
The file extensions that the malware is targeting contain certain clusters of formats including:
- Commonly used office file extensions (.ppt, .doc, .docx, .xlsx, .sxi).
- Less common and nation-specific office formats (.sxw, .odt, .hwp).
- Archives, media files (.zip, .rar, .tar, .bz2, .mp4, .mkv)
- Emails and email databases (.eml, .msg, .ost, .pst, .edb).
- Database files (.sql, .accdb, .mdb, .dbf, .odb, .myd).
- Developers’ sourcecode and project files (.php, .java, .cpp, .pas, .asm).
- Encryption keys and certificates (.key, .pfx, .pem, .p12, .csr, .gpg, .aes).
- Graphic designers, artists and photographers files (.vsd, .odg, .raw, .nef, .svg, .psd).
- Virtual machine files (.vmx, .vmdk, .vdi).
Sumann also gave tips on how to further secure your digital experience. Below is a set of tips to follow to secure your precious files from one of history’s worst cybercrime breakout:
- Enable strong spam filters to prevent phishing e-mails from reaching the end users.
- Scan all incoming and outgoing e-mails
- Enable automatic scans for anti-virus and anti-malware programs.
- Manage privileged accounts. Administrator accounts should only be used by those with the proper privileges or only during emergencies.
- Configure access controls.
- Disable macro scripts from Microsoft Office files transmitted via e-mail.
He also said that employee education programs should be done to help users in identifying scams, malicious links, and attempted social engineering.
Prevention is the best cure

Equipped with one of the most deadly combination of spread and penetrate, WannaCry demands in-depth measures for prevention, below are in-depth tips that might help you in protecting or recovering your data.
Countermeasures to prevent:
Administrators and End Users can take following preventive action to protect their systems :
- Microsoft Patch for Unsupported Versions such as Windows XP,Vista,Server 2003, Server 2008 etc.
http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598
- To prevent data loss Users & Organisations are advised to take backup of Critical Data
- Block SMB ports on Enterprise Edge/perimeter network devices [UDP 137, 138 and TCP 139, 445] or Disable SMBv1.
https://support.microsoft.com/en-us/help/2696547
- Apply following signatures/ Rules at IDS/IPS
alert tcp $HOME_NET 445 -> any any (msg:”ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response”; flow:from_server,established; content:”|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|”; depth:16; fast_pattern; content:”|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|”; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; classtype:trojan-activity; sid:2024218; rev:2;)
(http://docs.emergingthreats.net/bin/view/Main/2024218)
alert smb any any -> $HOME_NET any (msg:”ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Request (set)”; flow:to_server,established; content:”|00 00 00 31 ff|SMB|2b 00 00 00 00 18 07 c0|”; depth:16; fast_pattern; content:”|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|”; distance:0; flowbits:set,ETPRO.ETERNALBLUE; flowbits:noalert; classtype:trojan-activity; sid:2024220; rev:1;)
alert smb $HOME_NET any -> any any (msg:”ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response”; flow:from_server,established; content:”|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|”; depth:16; fast_pattern; content:”|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|”; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; classtype:trojan-activity; sid:2024218; rev:1;)
Recommended steps for Prevention:
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Establish a Sender Policy Framework (SPF),Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Don’t open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization’s website directly through browser
- Restrict execution of powershell /WSCRIPT in enterprise environment Ensure installation and use of the latest version (currently v5.0) of PowerShell, with enhanced logging enabled. script block logging, and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis.
- Maintain updated Antivirus software on all systems
- Consider installing Enhanced Mitigation Experience Toolkit, or similar host-level anti-exploitation tools.
- Regularly check the contents of backup files of databases for any unauthorized encrypted contents of data records or external elements, (backdoors /malicious scripts.)
- Keep the operating system third party applications (MS office, browsers, browser Plugins) up-to-date with the latest patches.
- Follow safe practices when browsing the web. Ensure the web browsers are secured enough with appropriate content controls.
- Network segmentation and segregation into security zones – help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
- Disable remote Desktop Connections, employ least-privileged accounts.
- Ensure integrity of the codes /scripts being used in database, authentication and sensitive systems, check regularly for the integrity of the information stored in the databases.
- Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA%, %PROGRAMDATA% and %TEMP% paths. Ransomware sample drops and executes generally from these locations. Enforce application whitelisting on all endpoint workstations.
- Deploy web and email filters on the network. Configure these devices to scan for known bad domains, sources, and addresses; block these before receiving and downloading messages. Scan all emails, attachments, and downloads both on the host and at the mail gateway with a reputable antivirus solution.
- Disable macros in Microsoft Office products. Some Office products allow for the disabling of macros that originate from outside of an organization and can provide a hybrid approach when the organization depends on the legitimate use of macros. For Windows, specific settings can block macros originating from the Internet from running.
- Configure access controls including file, directory, and network share permissions with least privilege in mind. If a user only needs to read specific files, they should not have write access to those files, directories, or shares.
- Restrict users’ abilities (permissions) to install and run unwanted software applications.
- Enable personal firewalls on workstations.
- Implement strict External Device (USB drive) usage policy.
- Employ data-at-rest and data-in-transit encryption.
- Block the file types:
exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf
Cloud Armor

Our expert opinion? Go with cloud.
Let’s be honest here. If the experts say that contacting the local government or the FBI is the safest way to treat an infection, then we all know that a backup is the only surefire way to secure all your company’s assets.
You might think that opting for a cloud solution against a global internet cybercrime is nuts, but BBC and Microsoft says otherwise. To them, WannaCry is a testament as to how much we badly need to take software and hardware updates seriously. Backup is the best solution, cloud is the best backup, you do the math.
With a cloud supported solution like Office 365 or an infrastructure with Azure support, you can kiss ransomwares like WannaCry goodbye as you go on your daily business life.
In times like these, nothing beats a partner that you can be comfortable with. Tech One Global with all its digital solutions is confident in providing the security that you need from on-boarding to 24/7 partner support. After all, it’s always nice to know that you can call experts when a desktop pop-up shows asking for $300 in exchange of your files.
Expect to see WannaCry make the headlines. Stay tuned because we’re going to give you more tools and in-depth methods to survive the biggest cyber threat in the history of the internet.
Inform your friends! Don’t forget to hit that share button.
Below are more tools for you to explore. Good luck! Don’t forget to contact us at info(at)techoneglobal(dot)com and we will try our best to provide technical support.
Tools to prevent: