Weeks ago, experts predicted that there will be stronger copycats of WannaCry. Enter Petya/GoldenEye “ransomware”, a threat that also leverages from the EternalBlue exploit. The two share a lot of traits: both spread easily, and both target high-profile entities like multinational organizations. The twist? It’s deadlier.
The current attack is like 2016’s Petya with added improvements like stronger encryption and more options to spread on. Some experts call it “GoldenEye” or “NotPetya,” while some stick to “Petya.” Compared to WannaCry’s astounding numbers (Around 200k to 300k global victims), Petya has less at around 2000. However,Petya is far more dangerous: experts assume that it’s a “wiper” masked as a ransomware. Wipers have one goal: to destroy files, and with the payment options looking flimsy at best, a Petya-affected computer has close to zero chances of recovery.
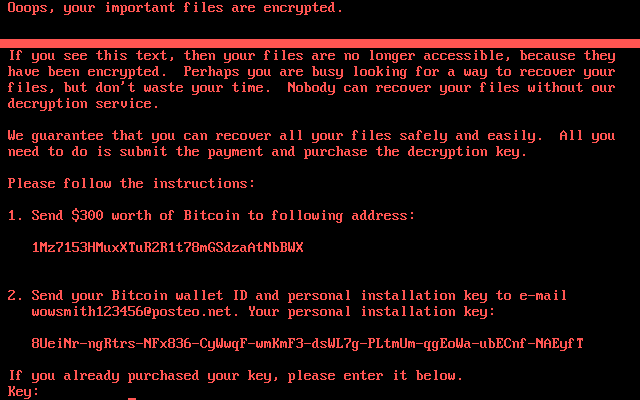
Similar to WannaCry, it targets the highest profiled victims like the Danish shipping giant Maersk and the public and private institutions in Ukraine and steals network administrative privileges to spread itself.
If WannaCry was a bombardment, Petya is a refined sniper with its scope on the highest commanders. WannaCry starts by penetrating networks and locking files, Petya goes much further: it steals administrative privileges. Putting it simply, once it affects a unit, it can then use its privileges to just instruct the other PCs connected to it to run the malware, which bypasses a lot of safety measures.
Ukraine suffered the brunt of the attack. As of now, its national bank, power company, and largest airport are all impaired. Even the deputy Prime Minister, Rozenko Pavlo, said that he and other members of the Ukrainian government cannot access their computers. ATMs are disabled and public transport, television, and postal services were also affected. It even reached Chernobyl where authorities were forced to switch to manual radiation monitoring.
Bitdefender Researcher, Bogdan Botezatu, emphasizes that the quality of ransomware code gets better with each iteration. Petya is a solid ransomware and experts are expecting a more sustained damage globally. One of the key pitfalls that WannaCry had is its killswitch. So far, Petya does not exhibit the same symptoms. Scary thought.
Petya has many parallels with WannaCry in terms of prevention. According to Sumann Subramaniam, Enterprise Security Expert at Tech One Global, the best course of action against the epidemic is still prevention.
How to Protect
- Ensure the latest Security updates installed and patch the system regularly. Keep the backups.
- Patch the EternalBlue (MS17-010) and disable the unsecured, SMBv1 file-sharing protocol on your windows systems.
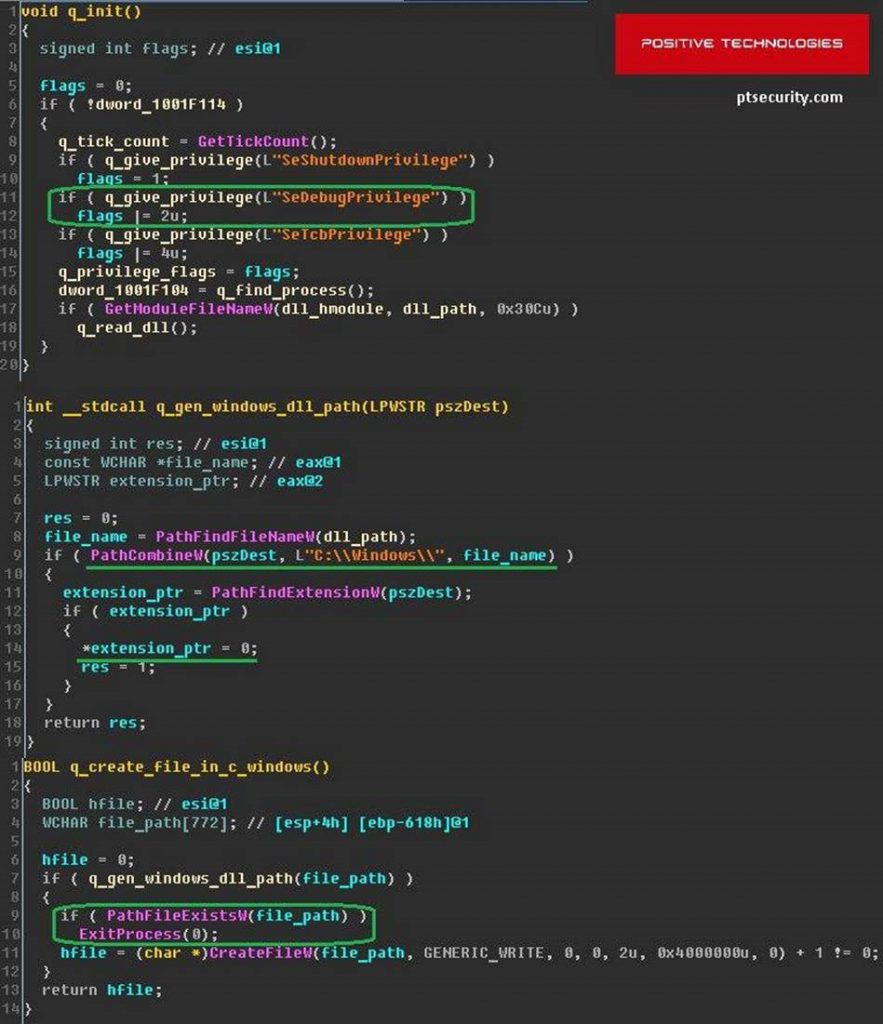
- Petya Kill-Switch: according to PT Security, users are advised to create file i.e. “C:\Windows\perfc” and set it to read-only to prevent ransomware infection.
- Do not reply to “Customer Service” to pay. The email is shutdown so there’s no way to get the decryption key.
- Always be suspicious of unwanted files and documents sent over email and never click on links inside them unless verifying the source.
- Ensure your antivirus guards are installed and updated. Ensure total security.
How to disable Petya from running
Create a file called perfc with no extension in %windir%
Steps:
- Open Notepad
- File
- Save As
- In File name type “perfc” with the quotations
- Save as type All Files
- Save this file in %windir% – put this in to the address bar
- Click Save
Note: these are good security defense-in-depth recommendations that may prevent being infected by this ransomware, but these steps alone do not guarantee against infection.
Below is a screenshot from ptsecurity.com showing the location of the killswitch:
It’s also continuously widening its target exploits. The ransomware also tried to take advantage of a related exploit to EternalBlue called EsteemAudit that is commonly found on Windows XP and Windows Server 2003. Thankfully, Microsoft already patched this problem as a preemptive measure.
Experts suggest that with a complex killswitch and the adapting nature of Petya, it’s here to stay. No single patch can counter it because of the many delivery options it has. Still, experts are encouraging continuous updates and patches as they are the only defense a normal person can resort to.
We are still at the tip of the iceberg and more news is to be expected within the next days, stay updated and secured. Stay tuned to Tech One Global.
Drop us a message, we’re here to help.